Urgent Alert: Cyber Offensive Targeting Israeli Web Infrastructure Amidst Ongoing Conflict
By Yinon Engelsman, Product Analyst & Cyber Security Researcher | November 8, 2023
As tensions escalate in the Middle East, a new cyber front has opened, bringing with it a wave of digital assaults against Israeli web assets. The Fatemiyoun Division, an Afghan Shia militia backed by Iran and known for its battlefield presence in Syria, has appeared to expand its operational remit to the cyber domain.
A series of destructive Iran-linked cyberattacks targeting Israel’s education and technology sectors was discovered by Palo Alto Networks’ Unit 42 research group and published last week. According to the group’s report, the attacks were tracked as far back as January 2023, and they continued as recently as October 2023 – after Hamas launched its surprise attack against Israel on October 7th.
Today (08/11/23), the Talon Cyber Threat Research team have discovered additional coordinated attacks against Israeli websites conducted by the Fatemiyoun cyber division with the following domains falling victim to these cyber strikes:
Https[:]//hard-wood[.]net/
Https[:]//info.maakav[.]net/
Https[:]//info.upschool[.]org.il/
https[:]//levhagalil-naz[.]co.il/
https[:]//tarekclinic[.]com/
Https[:]//mashhadts[.]com/
As of this morning, these digital platforms have experienced significant disruptions, including takedowns and defacements – hallmarks of a determined cyber gang operating under the Fatemiyoun umbrella.

The Israeli websites defaced by The Fatemiyoun cyber unite. Source: Https[:]//hard-wood[.]net/
The group has purportedly claimed responsibility via their Telegram Channel, aligning these attacks with the ongoing Israel-Gaza conflict.
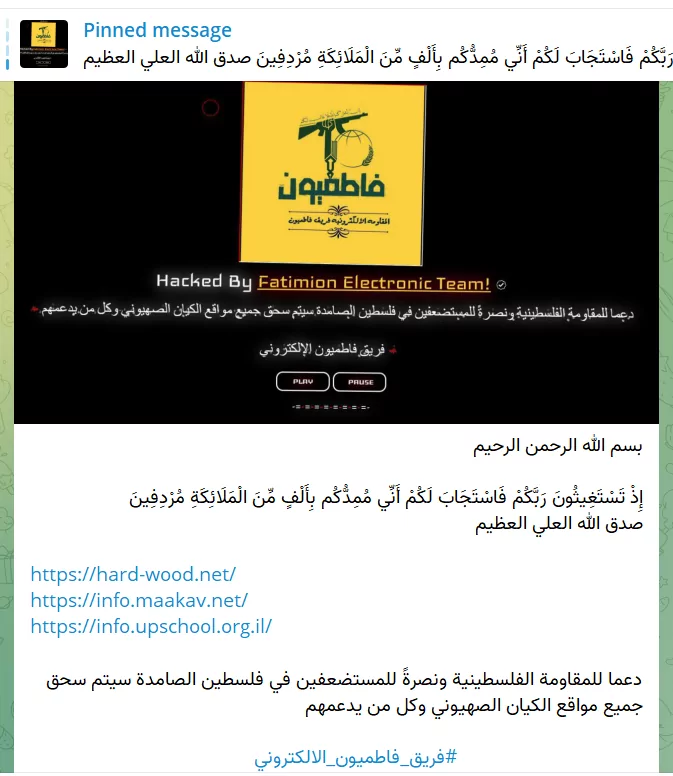
The Fatemiyoun division declared on the DDoS and defacement attacks. Source: The Fatemiyoun Division Telegram channel.
Immediate Steps for Web Administrators:
Incident Response Activation: If you suspect your network is compromised, activate your incident response plan immediately. This includes isolating affected systems, collecting and securing logs, and beginning the forensic process.
Enhanced Monitoring: Implement real-time monitoring for unusual activities indicative of a breach, including spikes in traffic, unknown IP addresses, and irregular access patterns.
Patch Management: Ensure that all systems are up-to-date with the latest security patches to close vulnerabilities that could be exploited in these attacks.
Backups and Redundancy: Maintain regular, secure, and redundant backups of all critical data and test your restoration processes to ensure they are effective.
DDoS Mitigation: Employ distributed denial-of-service (DDoS) mitigation tools to protect against overwhelming traffic aimed at incapacitating your web services.
Cybersecurity Training: Conduct regular training sessions with your staff to recognize phishing attempts and other social engineering tactics that could be used to gain unauthorized access.
Multi-factor Authentication (MFA): Implement MFA wherever possible to add an additional layer of security to your systems.
In light of the current cyber threats, it’s a stark reminder that vigilance is paramount. Cyber and phishing attacks are increasingly sophisticated and indiscriminate, affecting entities across the board. It’s essential for organizations and individuals alike to stay alert, enforce strong cybersecurity hygiene, and educate themselves on the signs of compromise.
As the digital threat landscape evolves, we advise all to stay informed, prepared, and protected. Reach out to cybersecurity experts for guidance on best practices and defensive strategies tailored to your unique needs. Remember, in cyberspace, the best defense is a proactive approach to security.
Stay safe and secure.
Recommended for you

How Talon’s Enterprise Browser Disarms Malicious Ads – Part 2
Today we're delving deeper into malvertising campaigns that have set their sights on Google Ads.

How Talon’s Enterprise Browser Disarms Malicious Ads
Let's delve into how the Enterprise Browser is architected to combat malicious ads.